In an increasingly interconnected world that relies heavily on electronics, security is paramount. Modern-day electronics almost uniformly rely on cryptography as the primary method to protect electronic data. Yet the budding research field of hardware security has proven that cryptography as we know it is not all that secure.
To this end, physically unclonable functions (PUFs) have emerged as a hardware security technique that offer everything from improved cryptography to anti-counterfeiting on ICs.
In this article, we’ll introduce the concept of PUFs, how they work, and how they work to protect data.
What Is a PUF?
Physically unclonable functions (PUFs) are a technique in hardware security that exploits inherent device variations to produce an unclonable, unique device response to a given input. On a higher level, a PUF can be thought of as analogous to biometrics for humans – they are inherent and unique identifiers for every piece of silicon.
Due to the imperfections of silicon processing techniques, every single IC ever produced physically differs from one another. From IC to IC, these process variations manifest in ways like differing path delays, transistor threshold voltages, voltage gains, and countless others.
Importantly, while these variations may be random from IC to IC, they are deterministic and repeatable once known. A PUF exploits this inherent difference in IC behavior to generate a unique cryptographic key for each IC.
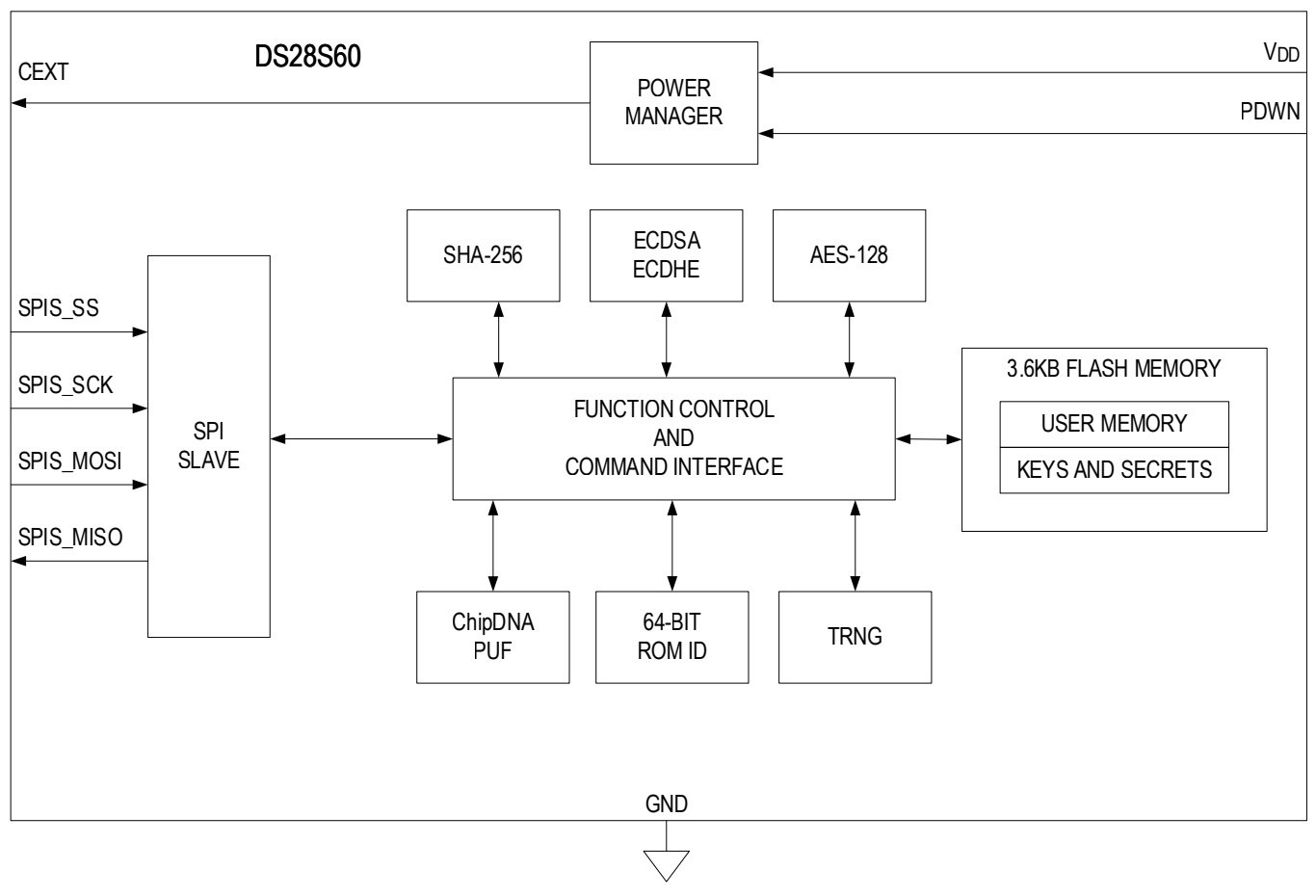
Figure 1. Maxim Integrated’s DS28S60 Coprocessor utilizes a PUF for cryptographic key generation. Image from Maxim Integrated.
Unlike a conventional cryptographic approach, which uses a single stored key, PUFs work by implementing challenge-response authentication. For a given PUF, a specific input, known as a “challenge”, will generate an output response that is unique to the specific PUF and therefore unclonable.
When manufactured, the PUF will be fed a series of different challenges and have its responses recorded. Through this exercise, the designers know each PUF’s unique response to a given challenge and can use this information to prevent counterfeiting, create and store cryptographic keys, and many other security feats.
A PUF Example
To better illustrate how PUFs work, we’ll take a look at a DRAM PUF—a PUF that exploits DRAM process variations to generate cryptographic keys and offer device authentication.
A standard DRAM cell works with a single capacitor to hold a stored charge as a binary state, and a pass transistor that controls the flow of charge to and from the capacitor. Due to device non-idealities, such as transistor subthreshold leakage, the charge on the capacitor tends to leak over time which causes the cell to lose state. This means that a fully charged DRAM cell representing a “1” bit value will unwantedly discharge to a “0” bit value over time.
Importantly for the purposes of a PUF, each individual DRAM cell leakage rate is highly affected by process variations in the cell’s manufacturing.
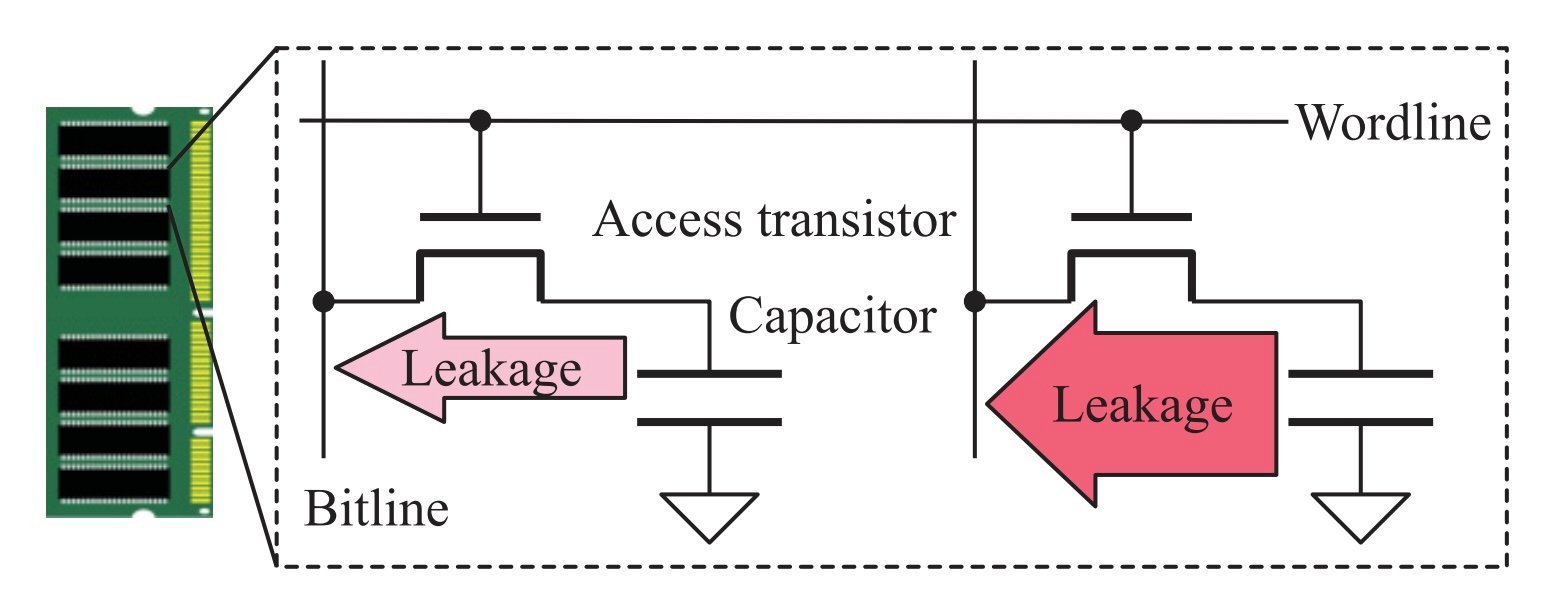
Figure 2. Charge leakage in DRAM cells is highly variable based on process variations. Image from Sutar et al.
To counteract this, all DRAM cells perform periodic refresh commands which reassert charge to “refresh” the storage capacitor. A DRAM PUF, on the other hand, works by pausing this refresh for a longer-than-usual specified interval of time and seeing how the cells have changed state due to leakage.
Since different cells leak charge at different rates, we can expect to see some cells fully discharge and change states within a time interval, while others may not have discharged enough to switch states at all.
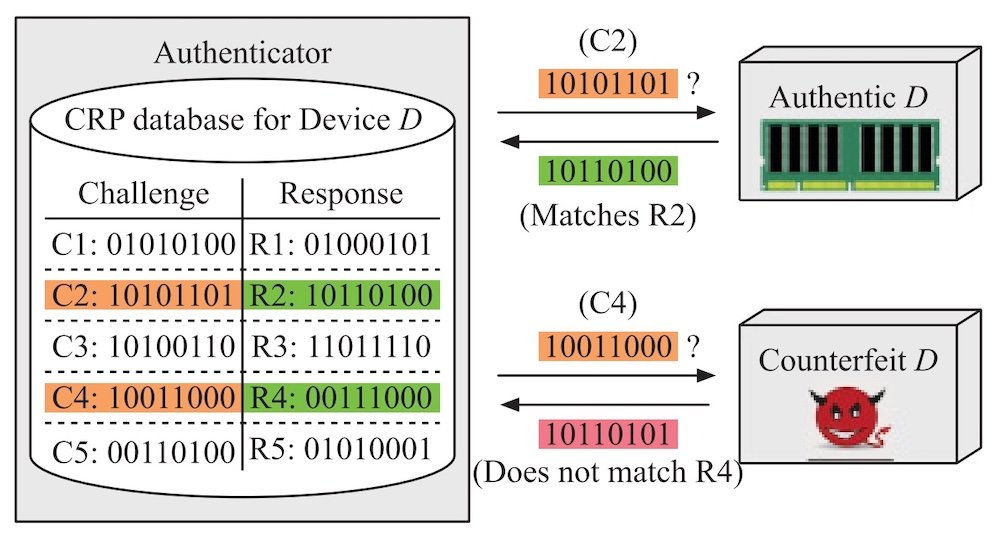
Figure 3. An authenticator may use a challenge-response pair database to authenticate a device. Image from Sutar et al.
In this instance, the “challenge” is the original binary value asserted to an array of DRAM cells, and the response is the value of that array after the given time interval. This technique may be used to generate truly random numbers for use in a cryptographic key generation, or it may be used for device identification for counterfeit protection. In the latter application, an authenticator may store a database of challenge-response pairs and use this knowledge to identify counterfeits vs authentic devices.
Benefits of PUFs
The advantages of using PUFs are tremendous, which is why the technology has found itself increasingly popular for hardware security.
For starters, one of the best features of a PUF is that it’s an inherently non-volatile technique, yet it doesn’t physically store any keys. Storing keys in non-volatile memory generally open up ICs to hardware attacks that allow adversaries to read memory content.
Instead, a PUF doesn’t store the key at all. It generates the key as needed as a response to a challenge, having the key instantaneously erased afterward. As Maxim Integrated put it: “there is always a key, but you can never look at it”. And even if you did try “looking at it”, attempts to probe PUFs can significantly affect their response to a challenge. Altogether, this makes the “storage” of a key extremely secure from attack.
Beyond this, a PUF benefits from being a true hardware solution. In the same way that a true random number generator can create truly unpredictable bit sequences, PUFs can create a truly unpredictable IC identifier or cryptographic key by exploiting true randomness in nature. This increases security since keys cannot be predicted based on some deterministic or quasi-deterministic process.
A Security Must
PUFs are a great option in hardware security thanks to their versatility – being useful in random key generation and storage, device authentication, random number generation, anti-counterfeiting, and much more.
In the next article, we will further discuss PUFs, how they’re characterized, and how they’re evaluated.
